The Internet of Things (IoT) is a new stage in the development of the Internet. Here more things connect to it than people. The transition to it happened in 2008-2009 when the number of devices in the network covered the Earth.
The IoT connects the objects around us into a computer network. They exchange information with each other and work without human intervention and in real-time. The introduction of the IoT became possible because of use of the Internet and gadgets. IoT systems consist of a network of smart devices and the cloud platform to which they are connected. They are used with systems for data, collected by sensors.
IoT is not one, but a whole stack of technologies, including IoT security testing. This is the creation of sensors and a variety of protocols for their interaction.
Why is IoT synonymous with poor security?
The security issue undermines the credibility of the Internet of Things. The hackers may steal data from IoT systems or sabotage production facilities. There were several such scandals in 2015. LG has admitted that its smart TVs share data with third parties. In the United States, a hacker hacked into a baby monitor and talked to a child at night.
So the participants in the IoT market will have to learn how to protect their systems. Cybersecurity of the Internet of Things is already being dealt with by Kaspersky Lab and other companies. That’s why iot penetration testing is rather important to find the issues.
IoT applications – consumer and enterprise
Consumer IoT devices must be controlled via an app, website, or screen on the device. Also, they must provide a specific consumer service, not just remote access to a smart home control system.
Of course, the ability to turn off the coffee maker from the couch is good. It’s even better if the sensor can read the time when I turn on the coffee maker. Then it will automatically prepare my hot drink every morning.
In every company, everything that connects to the Internet or a local network should be considered and controlled. If only because old “non-smart” devices can become a point of vulnerability to network attacks.
In corporations, devices connected to an intranet (or the Internet) also collect data. Then they provide information based on it, just as with the consumer Internet of Things.
Like consumer IoT, corporate networks can be chaotic and change frequently as devices move in and out of the network. But unlike consumer IoT, these networks can also coexist with other wireless or wired networks, such as fire safety or environmental control networks. Penetration testing services are aimed to find out problems and solve them.
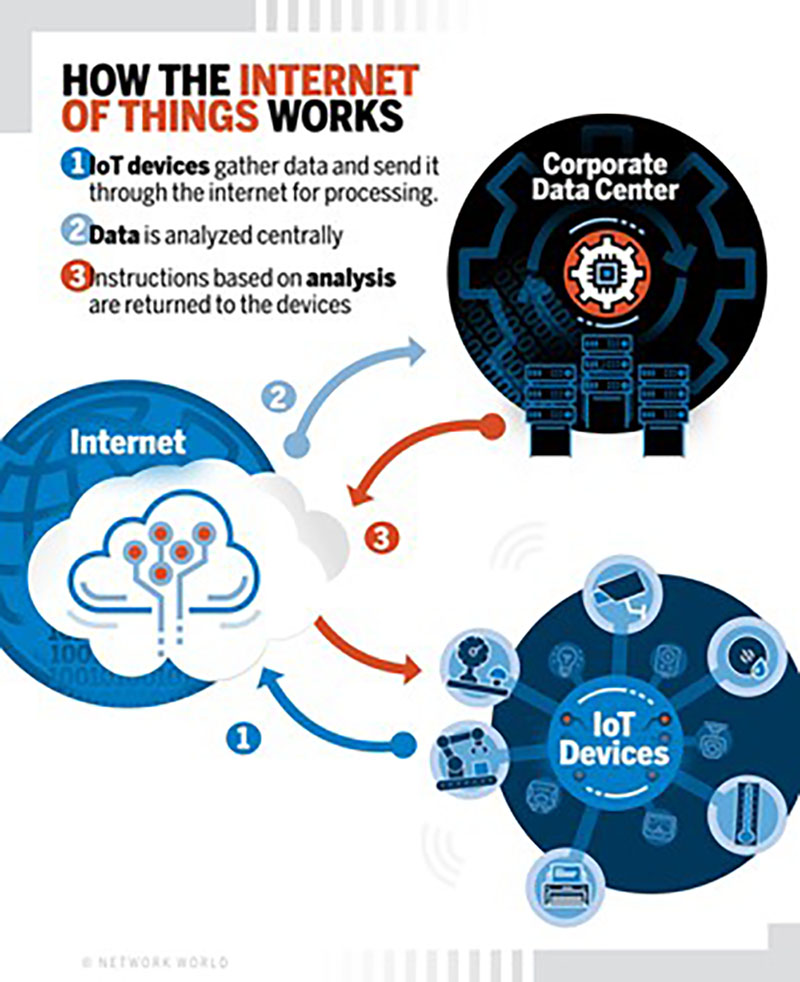
Vulnerabilities in IoT
ProIoT solutions are actively used today in urbanism, manufacturing, banking and insurance, aerospace, and telecom.
The main risks of information security in IoT for business:
- The rapid growth of infrastructure. The faster the number of IoT devices increases, the more reliable tools are required to monitor and manage infrastructure. If they are not there, attackers can use malware that will infect unprotected or misconfigured devices.
- Network connectivity. In the expanding IoT infrastructure of the enterprise, gadgets with different functionality and capabilities will certainly appear. The users need a reliable way to integrate these devices into a secure, end-to-end system. Professionals know how to test IoT security and are ready to carry out this task.
- Authentication. The lack of uniform standards for identification and authentication in a complex IoT environment is a serious problem. Because of this, it is impossible to establish trust relationships between individual IoT components, which is extremely important.
- User Account Control. Similarly, it is necessary to ensure the ability to securely manage user accounts of IoT systems and the systems themselves. Account data, even in large technology companies, is often stored in clear text, which is unacceptable.
- IoT devices are often assembled from solutions from different manufacturers. In most cases, the modern Internet of Things gadgets is assembled from typical components provided by different manufacturers. This saves time and money but seriously hurts device security.
Static and dynamic testing for IoT-connected devices
Static security testing begins early in the IoT lifecycle, can be manual or automated, and is, therefore, part of the verification process. This type of testing does not even require a computer in some cases – for example, when checking requirements. During dynamic testing, the external parameters of the program are checked: processor load, memory usage, response time, etc.


