Today’s business environment relies on a 24/7 network of third-party channels to meet consumers’ increasing demands. It’s now part and parcel for companies to engage various vendors and suppliers to facilitate processes. Unfortunately, working with the wrong third-party partner could result in potential legal, financial, and compliance issues. Such problems can be due to anything from poor customer service to cyberattacks. The latter is an area that is increasingly becoming a top priority among organizations.
The Devastating Consequences of Third-Party Risks
Cyberattacks due to third-party risks are devastating. Consider the Target and Equifax breaches that were caused by an associate’s weak credentials and application vulnerability, respectively. Target paid a fine of US$18 million, while Equifax had to shell out US$700 million to customers impacted by the attacks. Those amounts have yet to factor in the reputational damage.
Despite the lessons from these highly publicized attacks, third-party breaches continue to rise. Up to 59% of global companies have experienced a third-party-related cyber incident. Neglect is a primary reason, as organizations don’t focus on maintaining a healthy cybersecurity posture. Another reason is the tedious and outdated methodologies used in risk evaluation. Some companies still carry out a risk assessment using surveys.
The good news is that businesses are not defenseless against such cyber risks. Let’s take a look at how cybersecurity research tools such as Reverse WHOIS API and Reverse WHOIS Search can help.
How Reverse WHOIS API and Reverse WHOIS Search Can Help with Third-Party Risk Assessment
Reverse WHOIS API and Reverse WHOIS Search can be handy solutions used by infosec professionals for third-party risk assessment, threat hunting, and cyber investigation. By searching any identifier found in a WHOIS record, such as an individual’s or company’s name, or phone number, users can retrieve all domains whose records bear the information. Reverse domain lookups by email addresses are also possible with both solutions.
Here’s a hypothetical scenario: An account executive from FedEx pitched you a partnership opportunity. He gave you several flyers and resource materials that include the domain name fedex[.]com. To determine whether the agent is not just posing as a company employee, users can perform a basic reverse WHOIS lookup. They can also integrate the API into existing security solutions.
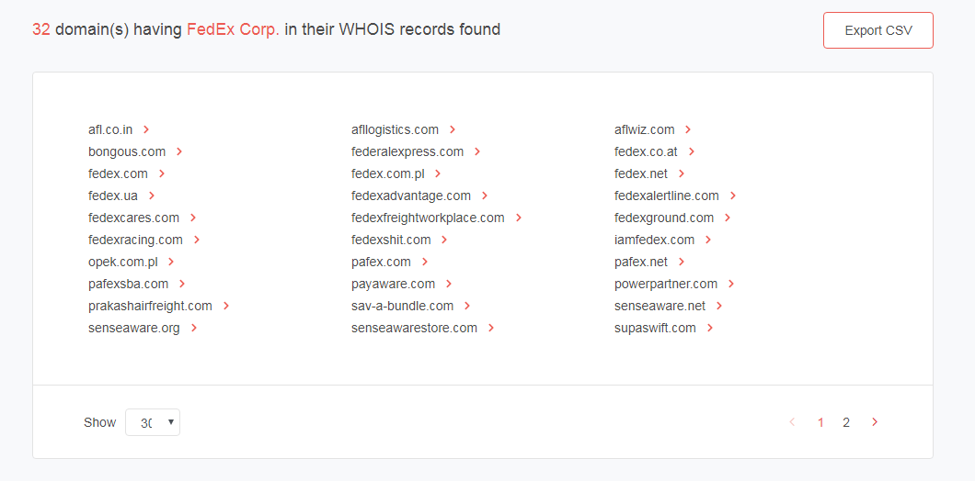
Let’s get to it using Reverse WHOIS Search. Since the tool did not return any result for “FedEx Corporation,” let’s use an alternative styling of the company name, FedEx Corp., as it appears in its corporate fact sheet. The tool returned 32 domain names. Fedex[.]com is one of the domains in the results. Click the red arrow beside the domain name to build a WHOIS or historic WHOIS report. Reverse WHOIS Search also allows users to add the domain to their monitoring dashboard.
We chose “‘Build WHOIS Report”’ from the options:
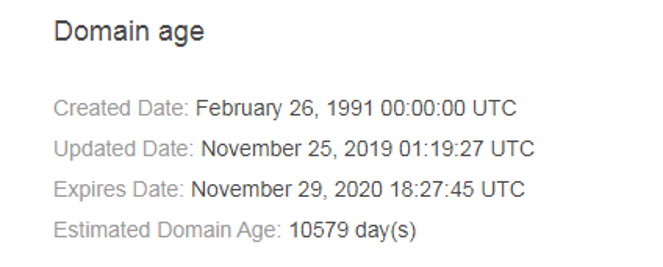
We found that the domain was created in 1991, making it close to 29 years old:
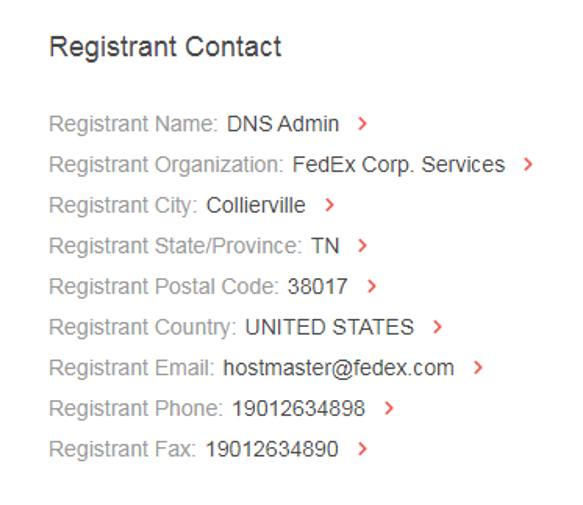
The data also showed that the registrant FedEx Corp. Services’s headquarters is in Collierville, Tennessee:
The report also revealed a few contact numbers. Note that dubious companies often conceal their WHOIS records from the public with privacy protection.
That is just one way of using the tool. Users can also compare the WHOIS record of a suspicious domain with that of its legitimate counterpart to see if there are inconsistencies. FedEx’s reverse WHOIS report revealed that it indeed owns all of the listed domains.
Users can also follow a similar process when verifying the legitimacy of a potential partner, or if they want to take a closer look at their individual web properties. Using the solutions, they can retrieve all their third-party partners’ domains to scan them for potential issues.
—
Third-party risks are inevitable so long as businesses outsource parts of their operations or share information systems with others. Organizations need to acknowledge that their cybersecurity plans should not hinge on contracts or promises made by third parties. They must take a proactive stance to quash looming threats in their supply chain. All this is possible with reliable threat intelligence obtainable from enterprise-grade research solutions like Reverse WHOIS API and Reverse WHOIS Search.
About the Author

Jonathan Zhang is the founder and CEO of Threat Intelligence Platform (TIP)—a data, tool, and API provider that specializes in automated threat detection, security analysis, and threat intelligence solutions for Fortune 1000 and cybersecurity companies. TIP is part of the WhoisXML API family, a trusted intelligence vendor by over 50,000 clients.