Organizations define their attack surfaces in various ways. In general, though, an attack surface can be generally categorized into the digital and the physical. But what is an attack surface, exactly? And why does it need identification and management?
What Is an Attack Surface?
An attack surface is simply all the ways that threat actors, or more loosely hackers, can get into and take control of a victim’s connected devices and applications. As mentioned, it can be classified into the digital and physical attack surfaces.
The digital attack surface refers to all vulnerable software, operating system (OS) services, web and desktop applications, and others. These don’t have physical forms. The physical attack surface, meanwhile, sums up all of a company’s hardware, basically any device that’s connected to the target network.
Any vulnerability left open to exploitation in applications and devices is an attack vector. And attackers typically use attack vectors to instigate a security breach.
Why the Need for Attack Surface Management?
Let’s face it, every organization today has some form of digital presence or does business online, which makes them likely targets of a malicious campaign. Some 540 data breaches in the U.S. have been publicized in the first half of 2020 alone.
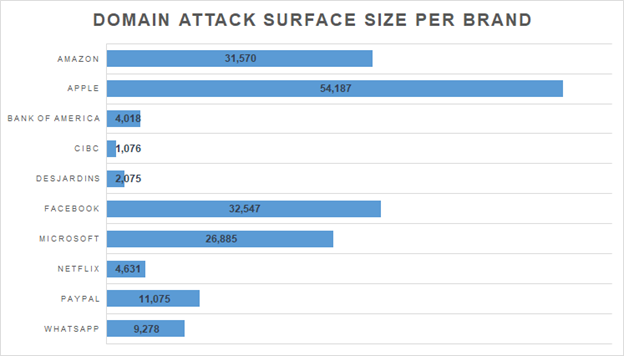
A study on the domain attack surface—a mere subset of a company’s total attack surface—of 10 of the most-spoofed companies also revealed that a victim could have as many as 17,734 domains and subdomains that hackers can use as attack vectors.
No matter how big an attack surface grows due to the millions of domain and subdomain additions each day, though, network protection remains doable with the help of attack surface management solutions from WhoisXML API.
How to Establish Your Domain Attack Surface
We identified three ways to gain awareness of and reduce an organization’s potential domain attack surface below.
Dig into Domains and IP Addresses
pDNS tools can give a comprehensive view of DNS records. For the aforementioned domain attack surface study, for instance, querying a pDNS tool for apple[.]com (the most exposed company) would give 18 records.
On one of these, you can find the domain’s corresponding IP address—17[.]253[.]144[.]10. Using it as a search term for a reverse IP/DNS lookup would provide an additional 40 records that point to related domains and subdomains, some of which may no longer be in use or insufficiently protected, thus widening Apple’s attack surface.
Audit Domains and Subdomains
As the featured study showed, an organization can own thousands of subdomains. A domains and subdomains discovery tool can enumerate a significant share of them. That would help detect and find unused domains and subdomains that may need deletion so they can’t serve as attack vectors. Hackers are known, after all, for hijacking forgotten domains to get into target networks.
Top notcher Apple in the said study, for example, turned out to have 54,187 possibly suspicious domains and subdomains. Two (apple-verification[.]cheapelectricnow[.]net and locked[.]appleid[.]apple[.]com[.]services-and-support[.]com), in particular, proved malicious.
Apple is, however, not alone in this situation, as some of the remaining companies’ names also seemed to be abused, as shown by the list of malicious domains below dubbed “malicious” on VirusTotal.
- amazon[.]co[.]jp[.]signin-id-234488990[.]checkidupdate[.]link
- sellercentral[.]amazon[.]de-verify[.]atulsave[.]in
- bankofamericaonlinesignin[.]elevator-love[.]com
- secure[.]bankofamerica[.]com-login-sign-in-signonv2screen[.]go[.]suzukihaiphong[.]com[.]vn
- www[.]m[.]facebook[.]page35683673645[.]com
- www[.]page-business[.]facebook[.]item872352783234[.]com
- microsoft-outlook-authenticate[.]ts[.]r[.]appspot[.]com
- microsoft-outlook[.]com[.]twinklelittlehouse[.]com
- netflix-update[.]fr[.]pvctamirikayseri[.]com
- netflix-global[.]auths-line[.]com[.]jagasia[.]co[.]id
- www[.]paypal[.]com-update[.]accounts[.]paypal[.]thepresidencyschool[.]com
- whatsapp-inviteme-joingroup18[.]2waky[.]com
- whatsapps[.]mrslove[.]com
—
The facts in the case study showed how big an organization’s domain attack surface can get. And that’s just one part of its overall attack surface. But as we also showed, establishing and managing attack surfaces is not impossible with constant vigilance and monitoring.