It can be frustrating for businesses to see a list of fake email addresses among their subscribers. And with hundreds of disposable email providers, this is nothing new or unique.
In fact, some websites even advice on how to save on Netflix subscriptions by signing up using a disposable email address and cancel the subscription before the 30-day trial period ends.
This kind of website abuse is not exclusive to online streaming sites. Most software-as-a-service (SaaS) companies face the same sales loss from both free trial periods and freemium offers. To illustrate this trend, we looked at two important questions in this post:
1. How Easy Is It to Obtain a Fake Email Address?
For sure website abusers use known email providers like Gmail, but they can also use disposable email providers such as 10MinuteMail, TempMail, and GuerillaMail. Why? The difference is the amount of time it takes to obtain an email address.
When using Gmail, for instance, you need to spend five minutes at the very least to create an email address. You need to make sure that your email address is unique, figure out a password that meets the provider’s standards, and give more personal details.
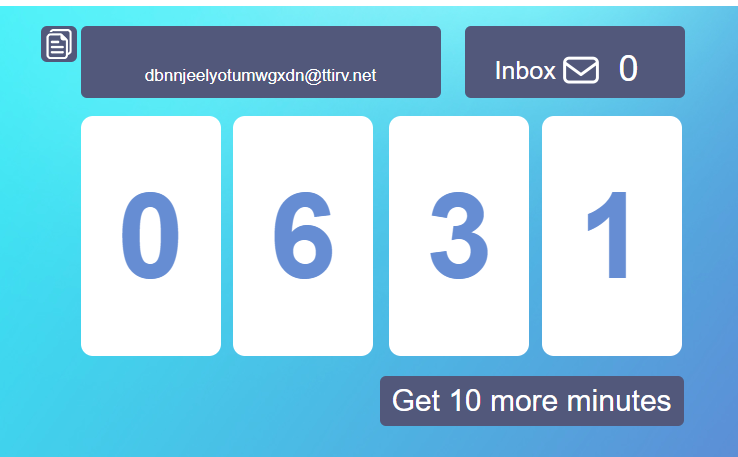
With temporary email providers, you can get an email address in a split second—as soon as you land on their website. When we visited the 10MinuteMail site, for instance, we were immediately given this random email address:
It’s easy to see why most website abusers use disposable and fake email addresses. So the logical way to stop them from abusing freemium and free trial services is to disallow disposable emails upon signup with a disposable emails database or an email verification API.
2. Do Disaposable Email Domains Really Work?
We came across an old question about a SaaS company that has a free user violating its freemium services. The user had 15 free accounts, although it’s not clear if he/she was using all of them. We visited the poster’s website to see if it already blocked users of temporary or disposable email addresses from signing up.
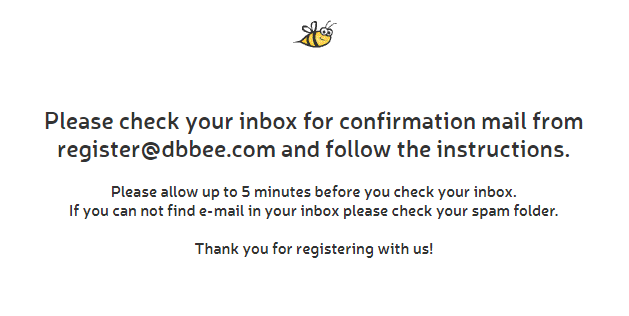
We used the temporary email address provided by 10MinuteMail earlier to go through the registration process of dbBee, the poster’s SaaS company.
The registration went through, and we were told to wait for the confirmation email.
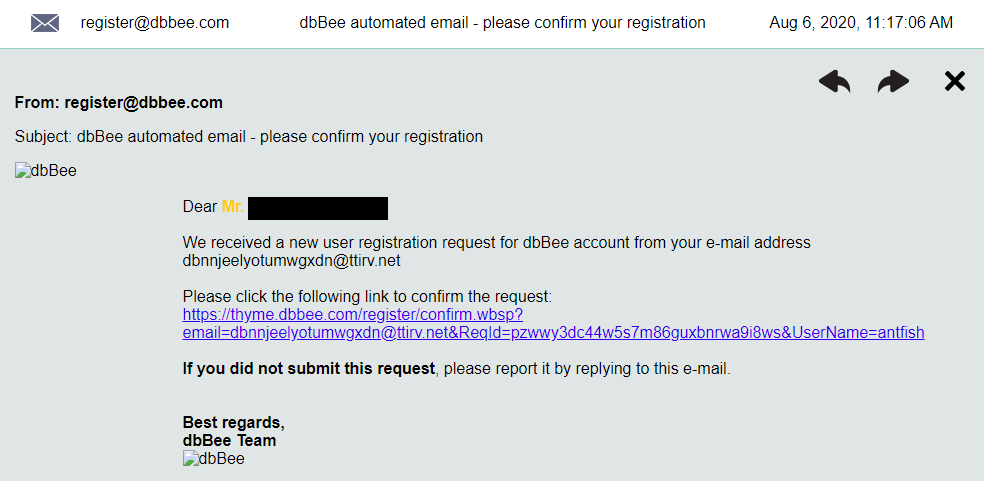
True enough, we received the promised email on our temporary account.
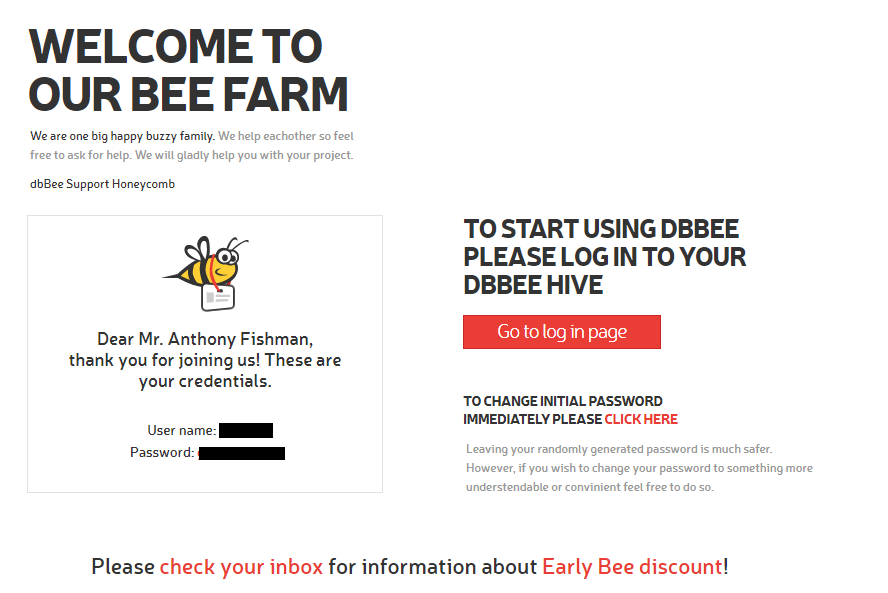
After clicking the confirmation link, we landed on the welcome page and was able to log in using the username and initial password provided.
We also tried using the same fake email address to sign up on Zoho Creator, another application development platform, and were able to sign up successfully.
Website abusers can follow the same process countless times to get several free accounts and work on as many projects they want. They would be using the SaaS company’s bandwidth and other resources without paying anything, making the company incur losses.
However, if dbBee, Zoho Creator, and other SaaS companies integrate a disposable email domains database into their signup pages, the email address we used would be tagged as “fake.” Below is a screenshot of a disposable email domain database containing a long list of fake email domains, including that of the service we used.
Conclusion
Website abusers can cause companies to lose a significant portion of their income as they take up bandwidth and other company resources without paying. Aside from that, users who signed up using disposable email addresses most likely can’t even receive marketing emails.
A fake email list can help ensure that only valid email addresses make it to your subscriber list. By preventing the use of fake email addresses during the registration process, companies can thwart website abusers.
About the Author

Jonathan Zhang is the founder and CEO of WhoisXML API—a domain and IP data intelligence provider that empowers all types of cybersecurity enterprises to build better products and achieve greater network security with the most comprehensive domain, IP, DNS, and cyber threat intelligence feeds. WhoisXML API also offers a variety of APIs, tools, and capabilities, including Threat Intelligence Platform (TIP) and Domain Research Suite (DRS).