You are most likely aware of what the Domain Name System (DNS) is and why it’s an essential component in the way the Internet works. For a comprehensive overview, you may want to check this DNS primer.
In a nutshell, one of the functions of the DNS is to translate domain names into IP addresses and vice versa. Every domain name resolves to an IP address, so when you input google[.]com into your browser, your computer sends a DNS query to a server so it can get the website’s IP address. The process only takes a second or less but it’s a crucial one.
Being able to check DNS name resolutions is also critical when it comes to cybersecurity. By knowing the connections between domains and IP addresses, you may establish links to cybercriminals’ domain infrastructure.
The challenge with DNS data, however, is that it only considers present connections. So, at least until the implementation of passive DNS, you couldn’t check what past connections were, say, a couple of weeks or months ago. The practical disadvantage of this was that cybercriminals could conduct a cyber attack by temporarily changing a domain’s record then putting it back the way it was later on to hide their tracks.
Passive DNS data is extensively collected by sensors of the network, detecting actual resolutions of domain names to IP addresses in the course of network communication, along with the timestamp when this resolution was observed. So, in addition to introducing time information, a passive DNS database is a source partially independent from the data stored in zone files or caches of DNS servers.
With that in mind, let’s take a closer look at some of the use cases of a passive DNS lookup and how it can be done in practical terms.
What Is a Passive DNS Lookup?
Passive DNS lookups can be done via a passive DNS database or by combining the capabilities of a DNS lookup web application and reverse IP/DNS lookup tools such Reverse IP API, Reverse MX API, and Reverse NS API that all offer timestamps for a given input.
Let’s take a look at an example.
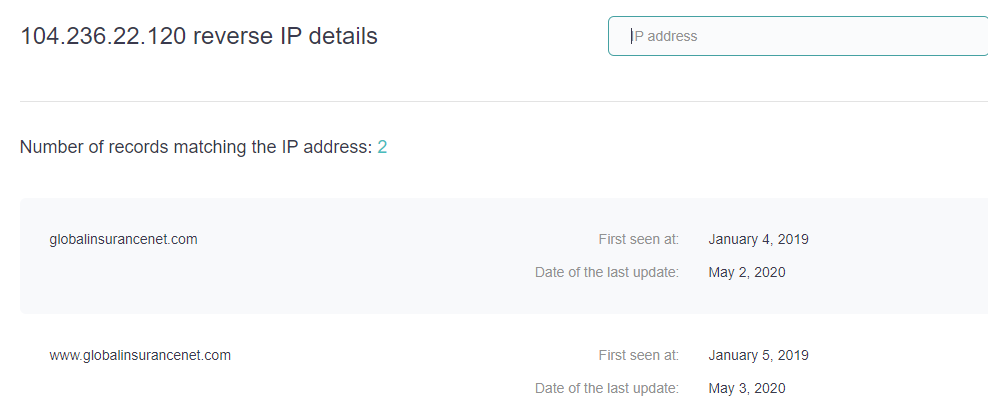
Even when globalinsurancenet[.]com changes its hostname or becomes a victim of cache poisoning, we would still be able to retrieve some of its zone data after performing a passive DNS lookup in two steps.
First, a regular DNS lookup would reveal the following details about the domain:
- IP address: 104[.]236[.]22[.]120
- Name server (NS): ns1[.]digitalocean[.]com
- Mail server (MX): west[.]smtp[.]mx[.]exch084[.]serverdata[.]net
Second, a series of reverse lookups would reveal further details. A reverse IP/DNS lookup tells us that on 4 January 2019, the domain was already resolving to 104[.]236[.]22[.]120.
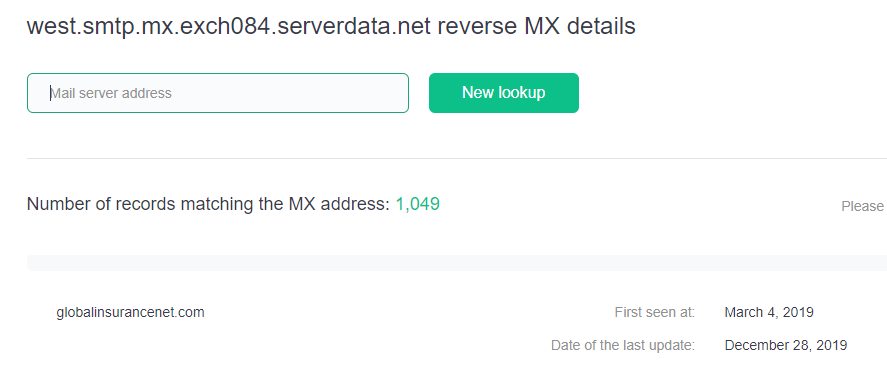
A reverse NS lookup would also reveal that the domain used the nameserver ns1[.]digitalocean[.]com from 1 March to 24 August 2019. Lastly, a reverse MX lookup tells us that globalinsurancenet[.]com used the mail server west[.]smtp[.]mx[.]exch084[.]serverdata[.]net on 4 March 2019.
Take note that we randomly selected the domain name globalinsurancenet[.]com from a passive DNS database.
Use Cases of Passive DNS Lookups
1. Recover Zone Data
Passive DNS lookups help organizations recover zone data even when it is modified, such as in the case of cache poisoning. Cache poisoning is a type of DNS attack that injects corrupted DNS data into the cache database. Such action allows attackers to redirect traffic to incorrect servers.
Whether due to cache poisoning or not, it’s good to have a time-stamped historical DNS records from passive DNS lookups on hand.
In globalinsurancenet[.]com’s case, its administrators can recover zone data from 2019 with the help of DNS and reverse lookups as illustrated in the previous section.
2. Look Into Malware Attacks
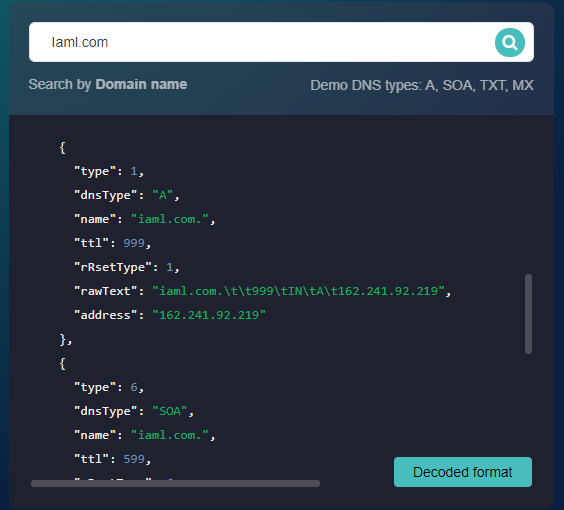
Take for example the domain laml[.]com, which is tagged as “malicious” on the Threat Intelligence Platform. According to the Bambenek Consulting OSINT data feeds, it is a botnet C&C host. Performing a DNS lookup on the domain would reveal that it resolves to the IP address 162[.]241[.]92[.]219.
Security teams can then proceed to run a reverse IP/DNS lookup to see other domains that have been associated with the IP address over time:
A deeper investigation on the IP resolution would reveal that 162[.]241[.]92[.]219 is also malicious, and is, in fact, an indicator of compromise (IoC) related to an Emotet malware attack on the United Services Automobile Association (USAA).
A look at the IP address’s DNS history would indeed reveal other associated domains for further scrutiny.
3. Map a Malicious Domain’s Possible Footprints
With the help of passive DNS data, security teams can see domain name resolutions and nameserver and mail server associations. From there, they can map the connected properties of a malicious domain name.
In our previous example, the DNS lookup on laml[.]com showed that it used the nameserver ns1[.]dnsnameservice[.]com and the mail server smtp[.]getontheweb[.]com. Using Reverse NS Lookup and Reverse MX Lookup would help security teams map out the malware domain’s connections.
Conclusion
The DNS will continue to be one of threat actors’ most favored attack vectors. As such, technologies that could help eliminate DNS risks are always welcomed by the cybersecurity community. Passive DNS lookups can further strengthen the cybersecurity posture of organizations, as these allow them to study historical DNS records.
About the Author

Jonathan Zhang is the founder and CEO of WhoisXML API—a domain and IP data intelligence provider that empowers all types of cybersecurity enterprises to build better products and achieve greater network security with the most comprehensive domain, IP, DNS, and cyber threat intelligence feeds. WhoisXML API also offers a variety of APIs, tools, and capabilities, including Threat Intelligence Platform (TIP) and Domain Research Suite (DRS).